
RANSOMWARE
Computer viruses are generally created to take over a small portion of your computer or smart device and make changes to the system files. They will mostly keep themselves hidden from the user while carrying out their purpose; stealing your personal information, spreading throughout a network, changing account settings to set up further attacks, etc.Most of the time, malware is automated. Cybercriminals are more likely to set up an attack and send it out via the internet (either through websites or email) than craft an attack against your specific system. The work/reward ratio is much higher for cybercriminals attacking thousands of systems per day (even one percent success may mean dozens of victims) than working hard to exploit your specific device/account.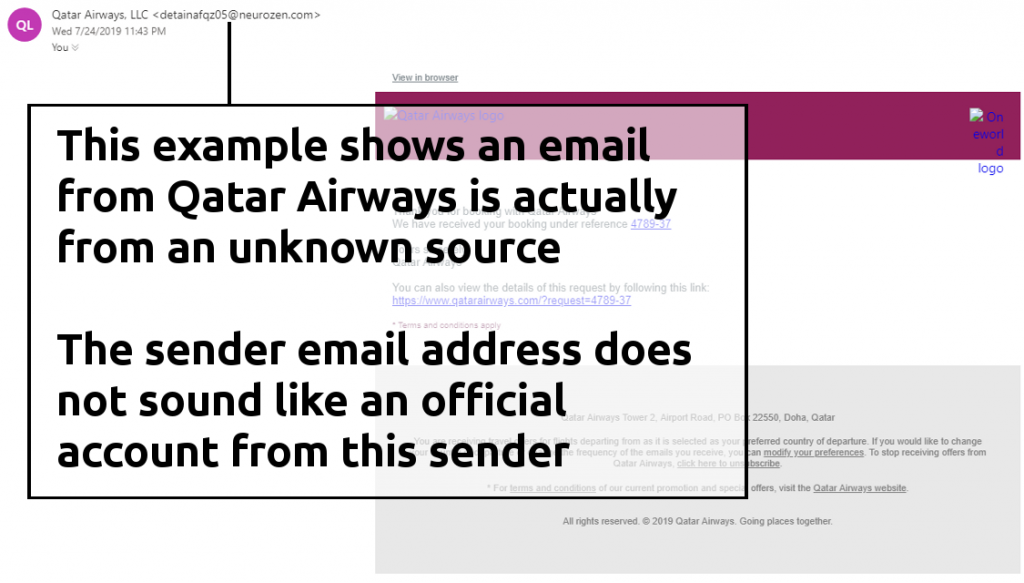
SOCIAL ENGINEERING
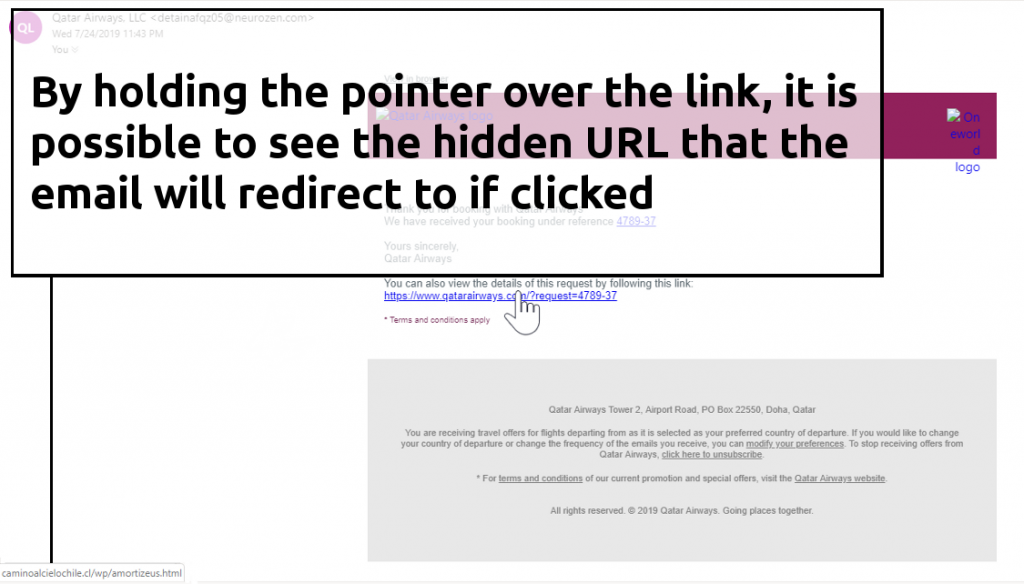
Social Engineering is the name given to communications that elicit a strong emotional response from the victim, hoping to trick them into acting before considering their actions. Telephone scams from people pretending to be from the Police or Banks demanding your personal information are examples of this. However, we will focus on social engineering emails.As with most cybercriminal activity, Social Engineering email attacks used to be very simple. A common example was the 419 scam; a Nigerian Prince asking for your bank account details so he can transfer millions of USD to you. It sounds foolish, but it succeeded in some instances. Similarly, scams may inform victims they have won a lottery or gained a massive inheritance from an unknown relative; all they need to do is provide personal information.As well as elation, Social Engineering attacks may try to use fear as the driving factor behind a campaign. Examples include blackmail threats, urgent action/payment or withheld services/deliveries unless the victim complies with the cybercriminal’s wishes. In a moment of panic, it is possible for the victim to accept the attack at face value and follow through with any request.SOFTWARE EXPLOITS
Software exploits are flaws or vulnerabilities in deployed software that cybercriminals will seek to take advantage of as part of an attack. Generally when a software company learns of an actively deployed vulnerability, they will modify their software so that it cannot be exploited. This update will be provided to users as a ‘patch’- it is important to patch software as soon as a solution becomes available to minimise the chances of being exploited.The most dangerous exploits are the ones that have not been patched and may only be known to the cybercriminal community. They will attempt to successfully compromise a system based on this vulnerability before news of the exploit becomes public and a patch can be produced. Zero Day Exploits are the names given to known vulnerabilities which are not yet patched by the developers.It is important to keep software updated and current to minimise the chance of becoming the victim of a software exploit.
PIRATED/STOLEN SOFTWARE
Related to SOFTWARE EXPLOITS, pirated software will often lead to problems on your system. The following holds true whether applying to software on a desktop/laptop or applications installed on a phone or tablet.Firstly, there is no knowing what a cybercriminal may have altered in the pirated software in order for it to be installed without a license. If they were able to change the source code to accommodate this, they could have changed the program to do literally anything else. Software will require administrative permissions to install; something which will give any malware free reign to make whatever changes to your system file it chooses.Secondly, even if there is initially nothing wrong with the pirate software there are rarely update services. Any exploits included in the software version installed will never be patched, offering an increasing number of entry points to your system as time passes.
STRONG/UNIQUE PASSWORDS
Most website and online services offer users the chance to create accounts to further their engagement on a platform. It is not uncommon for modern internet users to have hundreds of accounts at any one time. There are a few things that should be kept in mind when setting a password.When creating a password, it is best practice to ensure it is STRONG. This means that cybercriminals will have a hard time cracking (guessing) it. These criminals use programs to guess hundreds of username/password combinations every minute. The longer/more varied your password is, the less chance they have of cracking it. Weak passwords, such as ‘helloworld’, can be cracked in a matter of minutes. Passwords making use of letters, numbers, upper/lower case, symbols, such as ‘P@sswo&D3010!’, can take the same programs hundreds of years to crack.Having a strong password is one thing, but using the same password for every website/service will bring its own problems. If cybercriminals gain entry to a database with saved username/password combinations, then your personal information is still in danger. This is where the second password factor comes in.When creating a password, it is best practice to ensure it is UNIQUE. This means that you should never use the same password for more than one account. It may equally impractical to remember strong passwords for all your accounts. There are secure password services available that can remember them for you, often built into your web browser.Another option is to ‘salt’ the name of the website into each password (ie; ‘P@sswo&Dfacebook3010!’). To a human, it is easy to spot the word ‘facebook’ in that password and assume that to gain access to another account they might change the password to ‘P@sswo%Dtwitter3010!’, but a human is unlikely to read through the list of thousands of passwords from a compromised site to make this deduction. A variation on this suggestion will provide a strong, unique password for every site which is still easy to remember.
DATA BACKUP
Despite taking all precautions suggested here, it is still possible to lose access to your data. Ultimately, the best way to protect data from being lost to cybercriminals or system failures is to create copies of it. Ideally, copied data should be kept in triplicate. One copy should be made directly from your device (in the form of a physical disk or external hard drive) as well as creating another digital copy using a cloud storage service (Google Drive, Microsoft Onedrive, Dropbox, Mega, etc.).Having multiple backups will ensure that data can be recovered in the event of a malware attack, device failure or theft of a device. This applies equally to work files and personal files.ANTIVIRUS SOFTWARE
Antivirus software has increased in capabilities over the last few years, trying to keep pace with new malware types as they are developed. The Arms Race between virus and antivirus won’t ever end and there will be periods where cybercriminals have the upper hand. You should absolutely deploy an antivirus solution on your computer, but do not assume that this will keep you safe 100% of the time.As for most of the malware received by Silver Ridge, it can usually be detected by 50-70 of commercial antivirus solutions. Using your own judgement when connected to the internet and following safe data practices are also required to prevent you from becoming the victim of a cyberattack.Computer viruses are generally created to modify processes running on your computer or smart device and make changes to the system files. They will mostly keep themselves hidden from the user while carrying out their purpose; stealing your personal information, spreading throughout a network, changing account settings to set up further attacks, etc.
Most of the time, malware is automated. Cybercriminals are more likely to set up an attack and send it out via the internet (either through websites or email) than craft an attack against your specific system. The work/reward ratio is much higher for cybercriminals attacking thousands of systems per day (even one percent success may mean dozens of victims) than working hard to exploit your specific device/account.

RANSOMWARE
Computer viruses are generally created to take over a small portion of your computer or smart device and make changes to the system files. They will mostly keep themselves hidden from the user while carrying out their purpose; stealing your personal information, spreading throughout a network, changing account settings to set up further attacks, etc.
Most of the time, malware is automated. Cybercriminals are more likely to set up an attack and send it out via the internet (either through websites or email) than craft an attack against your specific system. The work/reward ratio is much higher for cybercriminals attacking thousands of systems per day (even one percent success may mean dozens of victims) than working hard to exploit your specific device/account.


SOCIAL ENGINEERING
Social Engineering is the name given to communications that elicit a strong emotional response from the victim, hoping to trick them into acting before considering their actions. Telephone scams from people pretending to be from the Police or Banks demanding your personal information are examples of this. However, we will focus on social engineering emails.As with most cybercriminal activity, Social Engineering email attacks used to be very simple. A common example was the 419 scam; a Nigerian Prince asking for your bank account details so he can transfer millions of USD to you. It sounds foolish, but it succeeded in some instances. Similarly, scams may inform victims they have won a lottery or gained a massive inheritance from an unknown relative; all they need to do is provide personal information.As well as elation, Social Engineering attacks may try to use fear as the driving factor behind a campaign. Examples include blackmail threats, urgent action/payment or withheld services/deliveries unless the victim complies with the cybercriminal’s wishes. In a moment of panic, it is possible for the victim to accept the attack at face value and follow through with any request.SOFTWARE EXPLOITS
Software exploits are flaws or vulnerabilities in deployed software that cybercriminals will seek to take advantage of as part of an attack. Generally when a software company learns of an actively deployed vulnerability, they will modify their software so that it cannot be exploited. This update will be provided to users as a ‘patch’- it is important to patch software as soon as a solution becomes available to minimise the chances of being exploited.The most dangerous exploits are the ones that have not been patched and may only be known to the cybercriminal community. They will attempt to successfully compromise a system based on this vulnerability before news of the exploit becomes public and a patch can be produced. Zero Day Exploits are the names given to known vulnerabilities which are not yet patched by the developers.It is important to keep software updated and current to minimise the chance of becoming the victim of a software exploit.
PIRATED/STOLEN SOFTWARE
Related to SOFTWARE EXPLOITS, pirated software will often lead to problems on your system. The following holds true whether applying to software on a desktop/laptop or applications installed on a phone or tablet.Firstly, there is no knowing what a cybercriminal may have altered in the pirated software in order for it to be installed without a license. If they were able to change the source code to accommodate this, they could have changed the program to do literally anything else. Software will require administrative permissions to install; something which will give any malware free reign to make whatever changes to your system file it chooses.Secondly, even if there is initially nothing wrong with the pirate software there are rarely update services. Any exploits included in the software version installed will never be patched, offering an increasing number of entry points to your system as time passes.
STRONG/UNIQUE PASSWORDS
Most website and online services offer users the chance to create accounts to further their engagement on a platform. It is not uncommon for modern internet users to have hundreds of accounts at any one time. There are a few things that should be kept in mind when setting a password.When creating a password, it is best practice to ensure it is STRONG. This means that cybercriminals will have a hard time cracking (guessing) it. These criminals use programs to guess hundreds of username/password combinations every minute. The longer/more varied your password is, the less chance they have of cracking it. Weak passwords, such as ‘helloworld’, can be cracked in a matter of minutes. Passwords making use of letters, numbers, upper/lower case, symbols, such as ‘P@sswo&D3010!’, can take the same programs hundreds of years to crack.Having a strong password is one thing, but using the same password for every website/service will bring its own problems. If cybercriminals gain entry to a database with saved username/password combinations, then your personal information is still in danger. This is where the second password factor comes in.When creating a password, it is best practice to ensure it is UNIQUE. This means that you should never use the same password for more than one account. It may equally impractical to remember strong passwords for all your accounts. There are secure password services available that can remember them for you, often built into your web browser.Another option is to ‘salt’ the name of the website into each password (ie; ‘P@sswo&Dfacebook3010!’). To a human, it is easy to spot the word ‘facebook’ in that password and assume that to gain access to another account they might change the password to ‘P@sswo%Dtwitter3010!’, but a human is unlikely to read through the list of thousands of passwords from a compromised site to make this deduction. A variation on this suggestion will provide a strong, unique password for every site which is still easy to remember.